Email authentication functions as both judge and executioner on the uncharted highways of email marketing. Why do we need it? And how to set it up? Learn more in this essential guide.
Bandits, robbers, and highwaymen followed humanity from behind natural covers since the beginning of civilization.
We like to think we’ve moved beyond these days. We did not.
The internet has opened up a world of opportunities for a whole new breed of highwaymen. Cybercriminals run a lucrative business out of hijacking emails. That’s why reputable senders must employ email authentication.
Back in the day, 1784 to be precise, John Palmer, an instigator for the British system of mail coaches, authorized the first armed postal coach from Bristol to London.
How did it work?
When approached by highwaymen, the driver urged the horses into a gallop while postal workers on the roof brandished muskets at the would-be thieves. Not surprisingly, the highwaymen turned tail and rode back into the forest.
This was just one of many things that the Post Office did to protect the mail.
Envelopes, proper addressing of mail, and advances in sealing technology were also introduced around this time.
It was very effective. Within 50 years, the number of mail robberies had dwindled to almost 0 in the UK. The same process happened later globally, and it didn’t take long for highway robbery to become a thing of the past.
How can brands make like the old-timey Post Office and protect their precious mail from cybercriminals?
The right authentication protocols will act like the envelopes, seals, and armed postal workers of olden times. They’ll protect both you and your recipients from fraud and other email-based forms of cybercrime.
In addition, it’s a matter of deliverability. You need your email authentication in place, like an armed mail coach, to get your campaigns into the inbox!
Here, we’ll go through everything you need to know in order to authenticate your emails and send them safely past all modern-day highwaymen.
First things first, open a domain
If you’re on top of your email/domain game, you can jump to point number #2.
The domain name is what appears after the @ when you’re sending out your emails. It acts like the postmark or franking mark on an envelope.
People are more likely to have confidence in a domain name they trust. A domain name that looks strange or unfamiliar might make users wary of clicking.
A domain name is an essential part of the relationship you build with your customers. Finding the right domain name is the first step towards establishing a mutual and trusting relationship with your audience.
Coming up with your domain name is a lot better than using the one that comes with your mail provider. There’s nothing wrong with an email that says “sent via Mailgun.org”, but it doesn’t appear incredibly professional. How would you like it if someone you were dealing with didn’t tell you their name?
What’s more, some SMTPs limit your sending volume when you’re not using your domain.
You could also open a few sub-domains in order to protect your domain’s reputation and improve deliverability. For example, you could open one subdomain for transactional emails and another for marketing emails.
In the postal coach analogy, sub-domains would be different kinds of coaches. The Post Office routinely fast-tracked important political correspondence in a ‘galloper’ coach, while less important personal letters trundled along at a slower pace.
How to open your domain?
Once you’ve decided on a domain name, you need to head up and register it on one of the many domain registrars available (GoDaddy, domain.com, Bluehost, and more).
Many domains have already been purchased, so when trying to register your domain name, you might be out of luck and in need of coming up with a different name. Remember, this is your brand, and it needs to be trustworthy.
Most registrars will charge you annually, with prices around $10 per year for your domain.
On top of that, there’s another $10 fee for privacy purposes, which we recommend to purchase.
Every domain has to have a registered owner. Without a privacy and protection pack, your information will be available for all to see.
This exposes you to pesky phone calls from people who want to purchase your domain, all the way to malicious attacks.
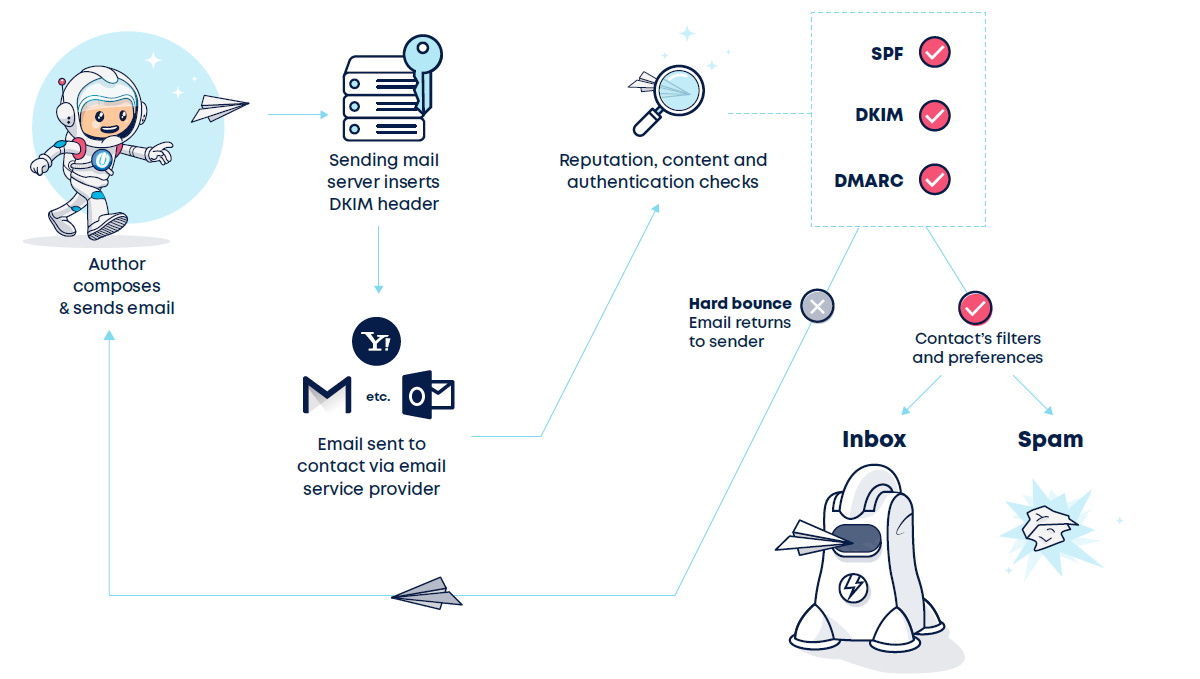
What are the different types of email authentication protocols?
There are three main types of email authentication protocols:
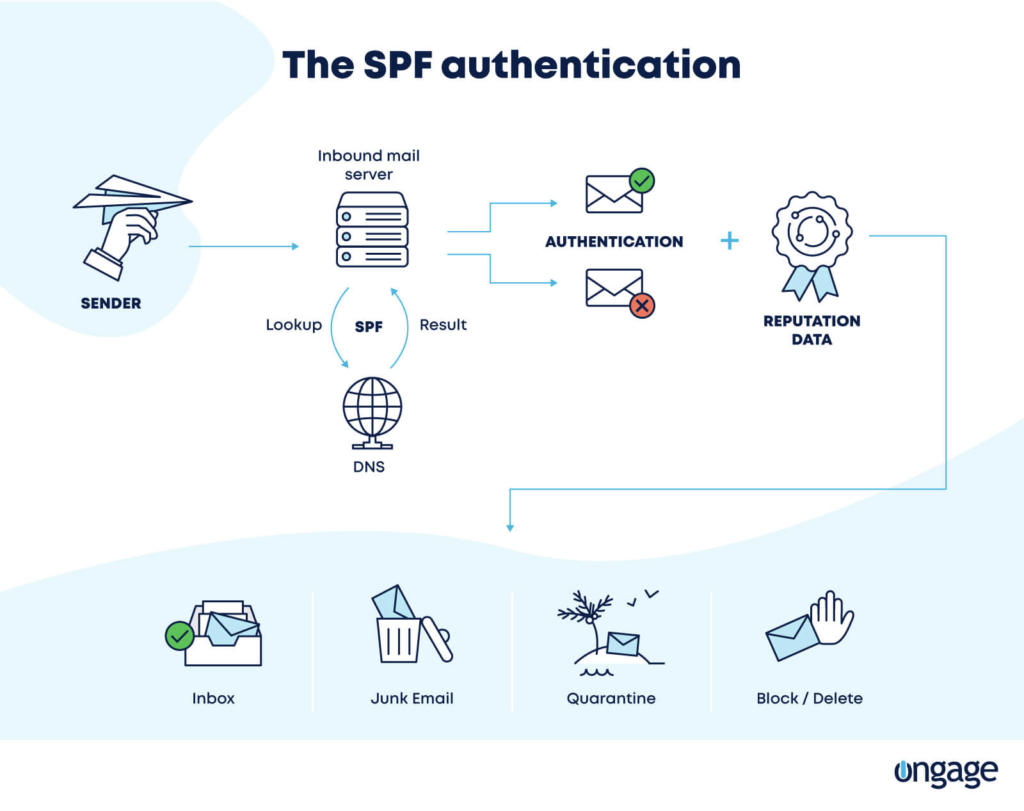
Sender Policy Framework (SPF)
An SPF protocol is among the oldest emails authentication protocols out there, but it still works well.
Essentially, an SPF checks out the ‘from’ address of an email, ensuring that the sender is who they say they are.
This is how it works:
- the recipient email server asks the sender’s domain to verify that the sender is authentic.
- It does this by requesting a list of IP addresses that are authorized to send from that domain.
- If the relevant server (the one from which the email is sent) does not appear on the said list, the SPF will ‘fail’ the email.
How to implement SPF?
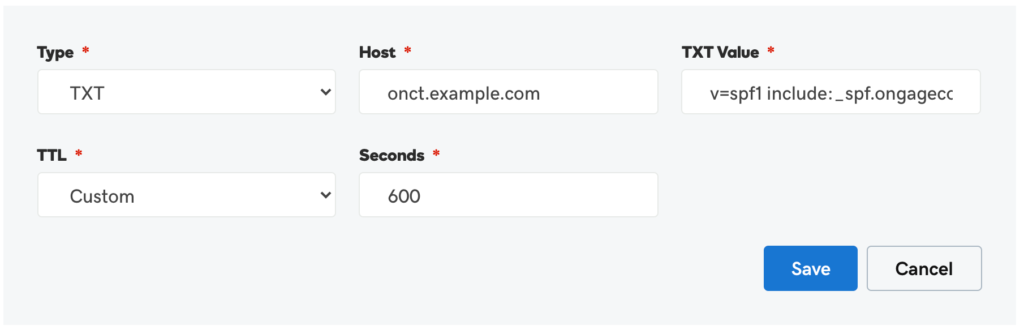
On your DNS, you will need to add a TXT record. This will look like this:
“v=spf1 include:sparkpostmail.com ~all”
To be on the safe side, it’s a good idea to visit your SMTP relay’s domain settings and copy the text provided into your DNS.
You should find it under ‘host’, depending on your domain hosting. Some will request that you type your domain in, while others will let you leave it blank.
If you use a subdomain, don’t forget to type that in as well.
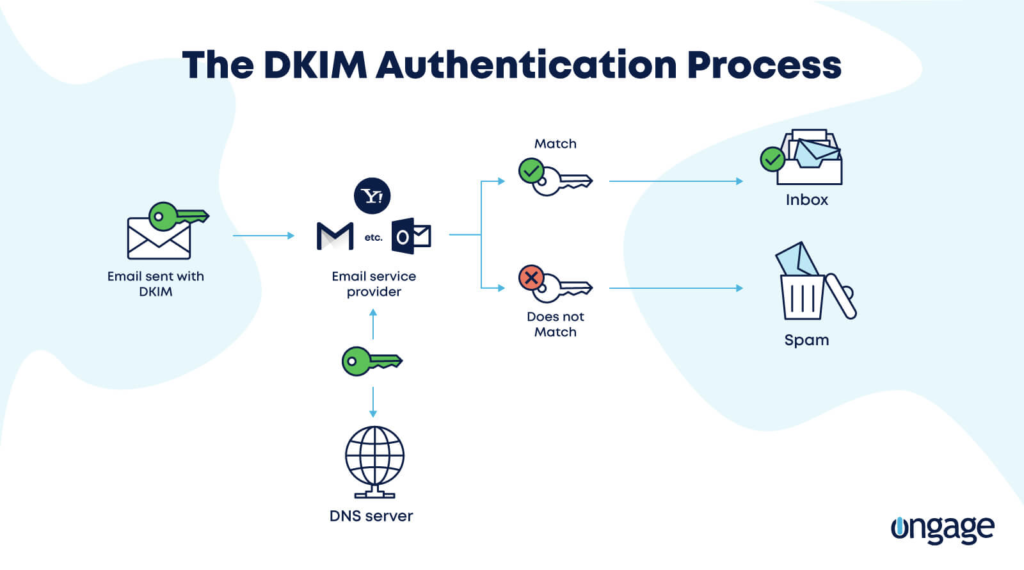
Domain Keys Identified Mail (DKIM)
DKIM is a bit tighter than SPF.
A DKIM protocol ensures that emails are tamper-proof by providing the sender with a private cryptographic key. This key encodes the headers of messages.
People opening the emails do so via a public key hosted on the DNS.
Any recipient can see the contents of an email using DKIM. Still, it is impossible for anyone other than the authentic user to send emails from that address (or tamper with emails en route) without the private key.
Think of it as an old-time letter seal. Until recently, many people had personal and highly individualized seals, which they would press into the wax to hold envelopes shut.
The correct recipient could still easily open and read the letter – but it was impossible for anyone to secretly tamper with the mail without their copy of the seal.
How to implement DKIM?
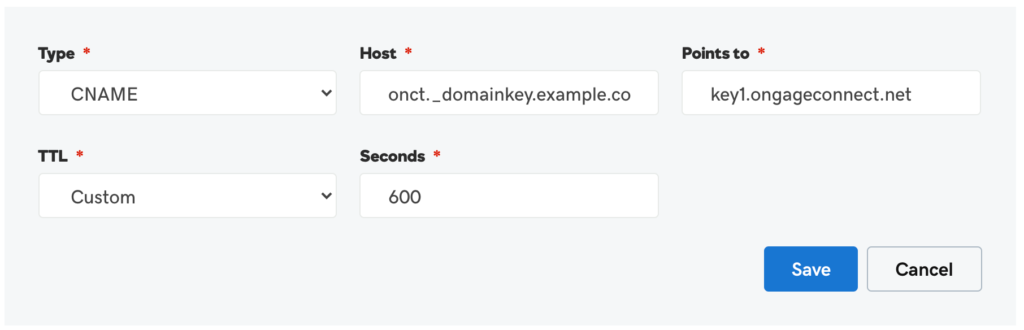
Unlike SPF, which works similarly in all SMTP relays, DKIM is unique for each domain.
In order to implement DKIM, head to the domain settings tab for your SMTP. The setting you want should look something like this:
k=rsa; t=s; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDPtW5iwpXVPiH5FzJ7Nrl8USzuY9zqqzjE0D1r04xDN6qwziDnmgcFNNfMewVKN2D1O+2J9N14hRprzByFwfQW76yojh54Xu3uSbQ3JP0A7k8o8GutRF8zbFUA8n0ZH2y0cIEjMliXY4W4LwPA7m4q0ObmvSjhd63O9d8z1XkUBwIDAQAB
You’ll probably also need to provide a hostname. For example, in Ongage SMTP, your hostname would be onct.e_{{yourdomain}}.com
The process for creating a DKIM CNAME will look something like the following:
Domain Message Authentication Reporting and Conformance (DMARC)
In the old days, postal coaches would be accompanied by a member of the staff. Some would function as coach drivers and delivery men. Others were armed protectors of the mail.
As well as outrunning and fighting off highwaymen, these mail mercenaries’ job was to consult with drivers and the coach inn staff along the way.
They’d talk to them about the safest routes to take, recent robberies, and dangerous characters to keep an eye out for.
DMARC works a bit like this. It builds on SPF and DKIM and provides a feedback system, granting senders more control over unauthenticated emails.
Why is this useful?
Senders can track fraudulent emails via reports and set up specific policies for ISPs when DMARC authentication fails due to SPF or DKIM failure (more on that later).
Overall, DMARC makes the email authentication system a lot more flexible on a human level while still maintaining security.
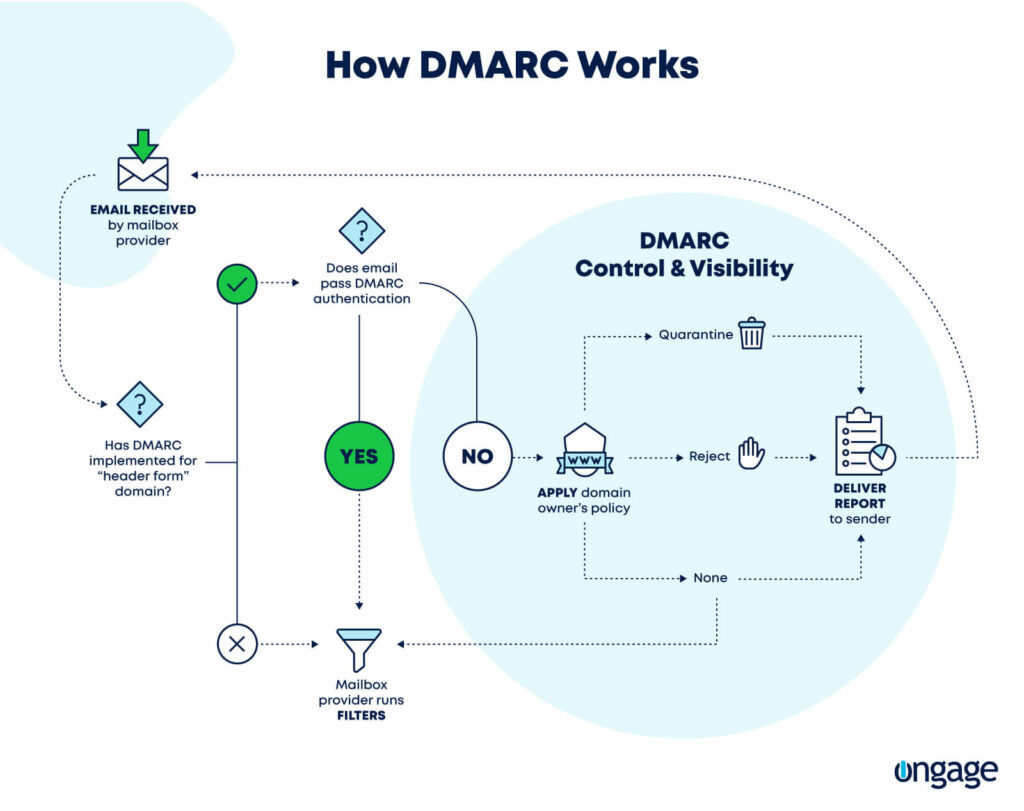
How to Implement DMARC?
To set up DMARC authentication, you will need to have already established either SPF or DKIM verification.
Unlike the other two, implementing DMARC doesn’t need you to go into your SMTP settings. Everything is done on the DNS side.
Under host, type in “_dmarc.{{yoursubdomain}}”.
The TXT text should look like this:
“v=DMARC1\; p=none\; rua=mailto:dmarc-aggregate@mydomain.com\; ruf=mailto:dmarc-afrf@mydomain.com\; pct=100”
Reading left-to-right in plain English, this record translates like this:
- v=DMARC1 specifies the DMARC version.
- p=none determines the preferred treatment or DMARC policy. In other words, it asks the ISP to do one of the following if DMARC authentication fails:
- None: treat the email as it would treat others without any DMARC validation. This is our recommended setting.
- Quarantine: accept the mail but place it outside the inbox (usually the spam folder)
- Reject: reject the message.
- rua=mailto:dmarc-aggregate@mydomain.com is the mailbox to which aggregate reports should be sent. Aggregate reports are XML feedback reports which explain why emails pass or fail authentication protocols.
- ruf=mailto:dmarc-afrf@mydomain.com is the mailbox to which forensic reports should be sent. Forensic reports are similar to aggregate reports, but they go into more detail regarding why specific emails have failed the protocols.
- pct=100 is the percentage of mail to which the domain owner would like to have its policy applied.
What are aggregate and forensic reports?
Both reports can be highly useful for tracking your entire email activity – authenticated or not – and we recommend requesting them by setting up an email address, as shown above.
Aggregate reports are sent every 24 hours and will show you all emails sent from your domain, and which passed/failed SPF and DKIM.
This is important for companies, as it can help them figure out if:
- Email authentication is working properly.
- Malicious actors may be spoofing your domain and attempting to phish your customers.
The problem is they’re very hard to read, which makes it impractical to translate them into actions. They need to be aggregated over time.
That’s why we advise using 3rd party services like:
- MXtoolbox delivery center.
- DMARC analyzer.
- DMARCLY.
Forensic reports (or failure reports) work a bit differently.
They are created in real-time and will be sent to the specified email address whenever a specific email fails the authentication test.
Moreover, they appear in plain-text (unlike the XML format of aggregate reports), making them much easier to read.
Depending on your needs, forensic reports might be more beneficial compared to aggregate reports.
Brand Indicators for Message Information (BIMI)
SPF and DKIM are the absolute minimum your business needs to maintain reliable deliverability. We’d even go so far as to say that DMARC is a necessity these days if you truly want to protect your domain and subscribers.
To dive even further, you can implement BIMI.
If SPF, DKIM, and DMARC are like sealing your letter in an envelope and sending it off in the postman’s trusty hands, BIMI is like doing all that – but in your own, personalized mail coach with your branding.
BIMI allows you to mark the mail as your own by showing your logo in the inbox, next to your message.
This is important because standing out in the increasingly crowded inbox is as important as email deliverability. BIMI gives your message (and brand) immediate visibility.

In this example, you can see how BIMI makes the email from Bank of America stand out in the Gmail inbox.
Adding identifiers like this also helps subscribers verify that the email they receive is truly from you. It’s a great way to crack down on fraudulent senders and to protect your brand’s reputation.
Verizon Media (AOL, Yahoo!, and Netscape) fully supports BIMI for a while now. In July 2021, Google officially announced that BIMI has finished beta, and that Gmail fully supports the new protocol.

How to implement BIMI?
Because BIMI means that every domain can use a different logo, every domain will need a different TXT record.
To get started with BIMI, you will need:
- To be DMARC verified.
- An SVG file of your logo (square-shaped).
- A DMARC policy (p=) of “quarantine” or “reject” for Verizon Media (AOL and Yahoo!). Otherwise, your logo will not display.
- To have a Verified Mark Certificate (VMC).
The protocol should look like this:
default._bimi.[Your Domain] IN TXT “v=BIMI1; I=[Your SVG’s URL]; a=[Your VMC URL]
Under host, use: default._bimi.{{yoursubdomain}}.
Having a VMC isn’t a must to have Verizon display your logo, but it is for Gmail. To obtain it, contact one of the following participating certificate authorities:
- Digicert – support@digicert.com
- Entrust Datacard – sales@entrustdatacard.com
Why is email authentication important?
Email authentication is a modern necessity. Like highway robbery in days of yore, cybercrime is a lucrative business, and everyone is a target.
However, there’s more to email authentication than simple security. These protocols increase deliverability by rendering your emails more trustworthy.
A triple-authenticated domain is more likely to hit inboxes and less likely to be consigned to Spam.
From a consumer point of view
Email authentication protocols are important because:
They reduce spam
According to Statista, around 50% of all emails sent are spam, and people hate it. Spam is, by definition, unwelcome. Many consumers welcome anything that will prevent their inboxes from filling up with useless, irrelevant, annoying spam.
However, spammers tend to get creative. They’re often very good at making their emails look – at first glance, at least – like the authentic, relevant content that people have signed up for.
By verifying that you do exist, that you are who you say you are, and proving this to the customer, email authentication makes it a lot easier to weed out spam and give audiences a much more fulfilling email experience.
They make it easier to avoid phishing
Phishing and other social engineering attacks often rely upon forged sender information. Email authentication protocols make such forgeries a lot harder to push through, and a lot easier to spot if they do get through.
By helping avoid phishing, authentication protocols give customers a safer experience and protect brands from the reputational damage of being associated with a phishing scam.
From a brand point of view
Email authentication allows your company to:
Raise trust in your brand
Email is often the main point of contact between consumers and brands.
Demonstrating that your emails are authentic and safe not only improves overall deliverability, it also makes it clear that you are taking precautions to keep valuable data safe and are therefore inherently trustworthy.
When the Post Office introduced postal coaches and other protocols to keep mail safe, its customers realized that the brand was very serious about its job. It was clear that the Post Office had a genuine desire to fulfill their customers’ needs.
This, more than anything, was what made the UK Post Office a nationally trusted institution, which eventually led to its model being copied worldwide.
Make your emails more reputable and secure
There’s no real reason not to put the most secure and rigorous authentication protocols for your email operations. Cybersecurity is a hugely important issue these days, and consumers won’t stick with your brand unless they can trust it.
Email authentication is your first line of defense against email hackers, and one of the simplest yet most effective methods of demonstrating your commitment to keeping your customers’ data safe.
They’ll improve your deliverability
If you suffer from low deliverability rates or open rates, one reason could be the lack of proper email authentication.
While trust and reputation are important in the sender-recipient relationship, implementing email authentication protocols is a must if you want to get into the inbox.
Without adding SPF, DKIM, and DMARC to your DNS, there are slim chances ISPs will let you into their inbox.
Bringing your email authentication A-game
Cybercriminals may not have the tricorn hats and gleaming horses of highwaymen like Dick Turpin, the royal mail coach’s menace, but they’re still dangerous. Whether they’re phishing, sending malware, or stealing data, they’re something that every email marketer should worry about.
By implementing email authentication and its protocols (SPF, DKIM, DMARC, and BIMI), you can protect your emails from modern-day ‘highwaymen’, and improve your deliverability at the same time.
At the very least, email marketers should have SPF and DKIM set up – but you can – and should – take things further with DMARC and BIMI.