You can do everything the right way. Set up an amazing infrastructure, write incredible copy, and still, your entire operation may come to a grinding halt. Why? Because of those pesky spam bots. Read on to discover why they’re so dangerous and how you can stop them from spamming your forms.
It was 1978, and the world faced a relentless foe.
Invaders from space that just wouldn’t stop coming!
They wore down your defenses, used up your resources, and seemingly grew smarter with each wave of attacks.
Space Invaders the game is as iconic as it was fun.
Spam invaders, the bots, not so much.
Spam bots are automated, relentless attacks that consume your website’s resources, bombard its sign-up forms, and, like the digitized alien enemies of Space Invaders, they keep getting smarter and faster.
Stopping them is necessary for proper email hygiene and the health of your list.
Why is that?
Because some forms of spam bots bombard your website or forum with automated bot comments that appear to be human in origin. These can overload your servers in one instance and impose into legit email addresses in another. Send emails to them, and you’re in hot water with ISPs and your ESP.
We explained how these malicious or “bad” bots assume different forms and perform various tasks meant to stimulate human interactions in our What is a Spambot? article.
In this article, we’re going to niche down and look at how to prevent spam bots from invading your subscription lists.
Discover why bad bots are filling out your subscription forms, how to prevent them, and what to do if spam bots have already invaded your subscription lists.
Form spammers and why they’re coming for your sign up forms
Spam bots that fill out email subscription sign up forms are bad bots.
These computer programs are built using algorithms or rule sets that instruct them to travel the internet and seek email subscriptions and other forms to complete.
Some bots are basic and can be easily repelled.
Advanced persistent bots are designed to mimic human behaviors and are more difficult to detect and defeat.
In addition to signing up for subscription lists, form spam bots complete the forms they find on websites to create fake accounts, download apps, simulate human engagement, distribute malicious links or malware, or support distributed denial-of-service (DDoS) or brute force attacks.
As for why they do what they do?
Form bots may be semi-autonomous, but they aren’t sentient. They do what their programmers or controllers have instructed them to do—over and over again.
What kind of damage can a form bot do to your business?
In the original Space Invaders game, players controlled a cannon to shoot at the incoming ships and defend the planet.
Players received 3 “lives,” meaning if the cannon was destroyed, the player received a replacement–but only twice. However, if an invader managed to reach the planet’s surface, it was GAME OVER no matter how many lives the player had left.
Spam bots are kind of that.
Defending against unwanted bot traffic, including spam bots, is critical for every online business. Without proper defenses, your website and your internal systems are vulnerable to cyberattacks, and your contacts’ data is at risk as well.
Bad bots:
- Consume your email marketing and contact management resources. Research indicates that 39% of all internet traffic is generated by bad bots. That’s a lot of bandwidth! Of course, spam bots make up just a portion of this whole and form bots even less.
Nonetheless, bots filling out your contact and email sign-up forms with false data is a real problem, particularly for brands that rely on healthy, engaged subscription lists to promote their goods and services. (Shouldn’t we all?)
Invalid email addresses and other entries will increase your per transaction or per session costs and force you to allocate more resources toward list cleanup, too.
- Skew performance metrics and reduce your email marketing effectiveness. Competitors or scammers that want to fill other brands’ email lists with bad data may send spam bots. Corrupt contact data and invalid email addresses introduced by form spammers can clog your subscription lists, reducing the effectiveness of your list segmentation and making your analytics reports less accurate.
- Damage your brand reputation and cause you to violate anti-spam laws. Bot owners who want to harm your brand can use your automated email marketing program against you as well. A malicious actor can flood your subscription list with real email addresses, giving the impression that the person has opted-in to receive your marketing content. Then, when your automated welcome message arrives in the email users’ inbox, they may mark it as spam or file a complaint with your brand. That’s not good for your domain or company reputation!
- Hijack your email lists to send spam or malicious messages. Some forms are vulnerable to hijacking, which can be accomplished by a bot that inserts specific code into the form. Once your form has been hijacked, a scammer can use it to send outgoing messages to the people on your subscription list. This method enables bad actors to send unwanted links, ads, or malware or launch a phishing campaign.
- Facilitate lead-generation fraud. Some fraudsters use form bots to get around the conversion requirement when executing click-fraud scams. They use bots to fill out a sign-up form to mimic a human lead making it appear as if the ad through which the bot clicked resulted in a conversion action.
- Support multi-pronged cyberattacks and introduce malicious code into your organization’s internal networks. Form spam bots can also be the tip of a spear aimed at identifying, testing, or creating vulnerabilities in your system. When your subscription form contains fields that allow unstructured (or semi-structured) entries such as street addresses or business names or ask registrants to enter a URL, this can create an opening to insert malicious content into your database.
- Compromise your data security and expose your contacts to risk. Malicious code introduced by a form bot can open a backdoor into your contact database and compromise your contacts’ data. Failure to protect subscribers’ data from bots can result in regulatory fines and reputational damage and the costs of mitigation.
- Bad bots put brand’s time, money and reputation at risk. IBM reports that in 2022, the global average cost of a single corporate data breach reached $4.35 million. The report found that it took an average of 207 days to identify a data breach and an additional 70 days to contain the breach once identified.
What are some signs that spam bots have targeted your sign-up forms and subscription lists?
The signs of a bot attack may be visible in your website’s analytics or list-building data.
For example, if your website’s sign-up page suddenly becomes a star attraction and gets a huge influx of touch-and-go traffic, this might be bot activity.
Similarly, fast bounces from page to page or incredibly short session times that appear outside the realm of human behavior may be signs that your website visitors aren’t human. 👽
A sudden spike in traffic from a geographic region or block of IPs may also signal a concentrated attack. Unless, of course, you’ve just executed an amazingly successful marketing campaign for that region. Be aware of your organization’s cross-channel marketing activities as you evaluate potential threats.
Your email list building and performance metrics can help you identify bot problems, too.
Within your list-building data, you may see signs of bot activity as a large increase in the number of sign-ups or a significant number of attempted sign-ups occurring in rapid succession.
A credential stuffing bot may enter a long list of email addresses one by one to test their validity–relying on your validation processes to do their work for them.
You may also notice an uptick in form abandonments if a bot is trying different addresses to crack credentials.
This stuffing strategy can also be used to identify which email addresses are associated with active subscribers.
If the bot attempts to register an address and gets a “this address already exists in our system” message, it now has more information to add to its profile about that email address’s user.
In subsequent phases, the bot may attempt to determine whether the subscriber has an account and then try to access that account data.
In your paid funnel, look for signs of fake form conversions by comparing the number of form fills to further conversion events and your costs per conversion. Bots may happily sign up for your subscription list, but their engagement and conversion rates just don’t stack up to those of real people. 📉
One obvious indicator that you are receiving fake sign-ups to your email subscription list is that the addresses entered are invalid.
Invalid email addresses are bad for your list-building efforts, and sending messages to those addresses will harm your deliverability.
They trigger hard bounces that make internet service providers think you aren’t engaging in good list-building practices. Plus, fake addresses represent junk conversions that can corrupt your performance and attribution metrics.
Not every invalid entry is the work of a spam bot, though.
Humans make errors when entering their email addresses and sometimes intentionally enter fake addresses to avoid sharing their credentials with businesses. Real people can also use temporary email addresses to access your list.
If you want to know if you are dealing with people or bots, examine the source and cadence of invalid entries.
For example, if you see an influx of invalid emails all generated by data center IPs, it’s unlikely that human error is the cause.
Compare website traffic and form activity data points to detect patterns that point to high-volume attacks.
Monitor your email bounce rates as well.
If an invalid email slips past your defenses, the messages you send to that address won’t slip past ISPs. Hard bounces are a sign that there’s something wrong with your address list. You’re sending messages to email addresses that don’t exist or have been permanently disabled.
An increase in your invalid email counts and hard bounces can alert you to bots that are entering fake credentials.
But bots may enter real addresses into your form, too.
A bot may sign up using real peoples’ addresses without their consent or add spam trap emails to your list to sabotage your sending and domain reputation. Eek!
Keeping an eye on your spam complaint rates and sender reputation scores will also help you spot bot activity aimed at tricking you into spamming email recipients.
14 tactics to protect your brand from form bot spam
Keeping the spam bots from overwhelming your website, corrupting your data, and impairing your real users’ experiences requires companies to be as adaptive and innovative as the enemy they face.
Simple defenses will repel the first wave of basic bot invaders. But you’ll need to up your game to push back against more sophisticated attacks.
To beat the bots, employ a multi-stage defense that combines:
- Automated screening systems that identify and repel spam bots.
- Digital obstacles that thwart bot attacks.
- Data hygiene programs that quarantine, clean and eliminate bad data regardless of the source.
Spam Bot Deflection Stage 1: Form-level defenses against spammers
Incorporate anti-bot measures into your website forms to slow the progress of these unwelcome visitors.
Ask a challenge question that bots can’t answer
An unexpected question can thwart a basic spam bot and cause them to abandon its efforts or enter a wrong answer that gives them away. Challenge questions require the user to read a query and enter an answer.
Most of these questions involve asking the person a simple math question because this enables your form to detect right and wrong answers easily.
The single correct response to “What is the sum of 3 plus 4?” is much easier to monitor and check than the many possible responses to a question such as “What is your favorite color?”
Allowing your field to accept multi-character answers like “periwinkle blue” can also open your form up to malicious code entries.
Logic problems that require the visitor to perform multiple tasks to arrive at a single answer can avoid the issues of clever bots and open-ended answers, but not without a human cost.
For example, a form might ask users to multiply 6 times 8, then enter the sum of the answers’ digits in the field (6 x 8 = 48; 4 + 8 = 12). Ngl, there’s a good chance I wouldn’t pass this one before I’d had coffee.
In terms of effectiveness, the easier a question is to answer, the less effective it will be at stopping bots. The harder it is to answer, the more likely it is to annoy legitimate subscribers.
Use a classic CAPTCHA to block the spam bots
Technically, most challenge questions meet the criteria to be considered a CAPTCHA or a “Completely Automated Public Turing test to tell Computers and Humans Apart.”
The questions aren’t hidden and the results can be assessed automatically. But there are a lot more ways to CAPTCHA out there–some more effective than others.
Like simple questions, simple CAPTCHAs, such as the classic click on every stoplight or type the numbers or letters you see, aren’t as effective as they used to be.
Bot builders use what they learn from each attack to improve their code and overcome web owners’ defenses. And when all else fails, a bot’s human controllers can hire people to solve the CAPTCHAs their bots encounter.
CAPTCHA’s effectiveness as both a bot blocker and a human access granter is questionable. How many times have you failed a CAPTCHA? (Or is that just me.) Annoying for anyone, visual-based CAPTCHAs also present accessibility problems for some of your website’s visitors and may make them feel unwelcome.
Want to find out what your audience thinks of CAPTCHAs? Head over to that famous feathered social media platform and search for “prove I’m human.”
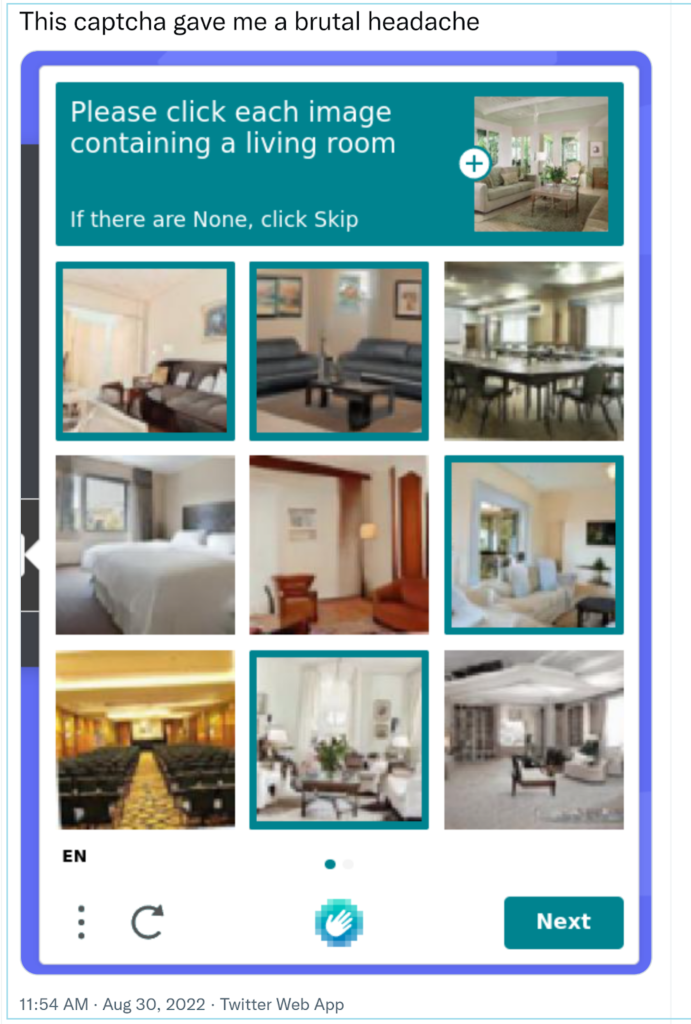
This Twitter user reports that the image-based CAPTCHA they’ve shared asking them to choose only those interiors that represented a living room “gave them a brutal headache.”
Audio CAPTCHAs are an alternative to image-based challenges.
An audio CAPTCHA allows visually impaired users to complete the requested task. However, these CAPTCHAs present many of the same obstacles for users as visual ones, and they force users to turn on their sound.
In general, any interactive element that asks your website guests to perform a task may communicate that you are outsourcing your cybersecurity to your customers.
What about reCAPTCHA or noCAPTCHA?
ReCAPTCHA is one of Google’s public Turing test tools, and it allows users to prove their humanity by checking a box next to the text “I am not a robot.”
Checking the box isn’t really the thing, though. It’s not as if a robot couldn’t just lie, right? Instead, the reCAPTCHA algorithm examines how the entity checking the box moves their mouse or gestures between fields and between the box and the submit button.
Google’s one-click reCAPTCHA box.
This system is sometimes called noCAPTCHA because it doesn’t include the usual problem-solving element. Unfortunately, if your moves are too fast and smooth, you still have to complete a standard CAPTCHA test.
Even though reCPATCHA uses the iconic “I’m not a robot” text, a noCAPTCHA doesn’t have to mention robots at all.
For example, your form’s “confirm your wish to opt-in” or “sign me up” checkboxes can be noCAPTCHA input points. This tactic allows your algorithm to collect the data it needs without asking your subscribers to do extra work.
Up your CAPTCHAs with score-based or invisible options
These are the latest CAPTCHA upgrade and don’t require user interaction. To use this type of system, you install a key on your website that monitors visitor activities and scores their behavior across a number of metrics.
For example, a human seldom moves from one point to another in an entirely straight line, especially if they aren’t trying to. So direct linear movements from field to field might make the algorithm suspect the visitor is a bot.
Another giveaway is speed. Even using auto-fill, there are limits to how fast a person can zip through a form and select the submit button. Finish the entire task in milliseconds and you’ll be accused of being a spam bot.
Both motion and time analysis may be used to score the likelihood that a website visitor is a bot. Google’s reCAPTCHA v3 uses a scoring system and permits website administrators to decide the cutoff score for their site. Vendors, such as hCAPTCHA, provide a selection of CAPTCHA and noCAPTCHA formats from which website owners can choose.
Employ real-time field validations
Real-time field validations are a series of rules or checks that automatically assess a form’s data as it is entered. The information may be checked to ensure that it meets the data field’s parameters or screened for malicious or invalid inputs.
For example, validating an email field begins with a syntax check. The form parameters would require that any entry in this field have an “@” and a domain address (e.g., “gmail.com”).
Additional behind-the-scenes checks verify factors such as the existence of the email domain and the IP address.
Field validations can be incorporated into your form’s code, performed using third-party services or by combining these methods. You can include forbidden content parameters in your validation rules, too.
In the case of an email address, you might create an input rule that prohibits email addresses from specific domains, such as those associated with spammers or temporary email addresses. Some B2B brands prohibit sign-ups using non-business email addresses with this method.
Field validation isn’t just for email addresses, either. Use input rules to prohibit the entry of URLs or code snippets in your form’s name, address, or other text fields and screen these fields for suspect entries.
You can use a shipping address verification app to review purchasers’ addresses for typos or missing information and confirm that the address actually exists, and more sophisticated verification services to correlate the information provided by a user across different data sets to confirm its accuracy.
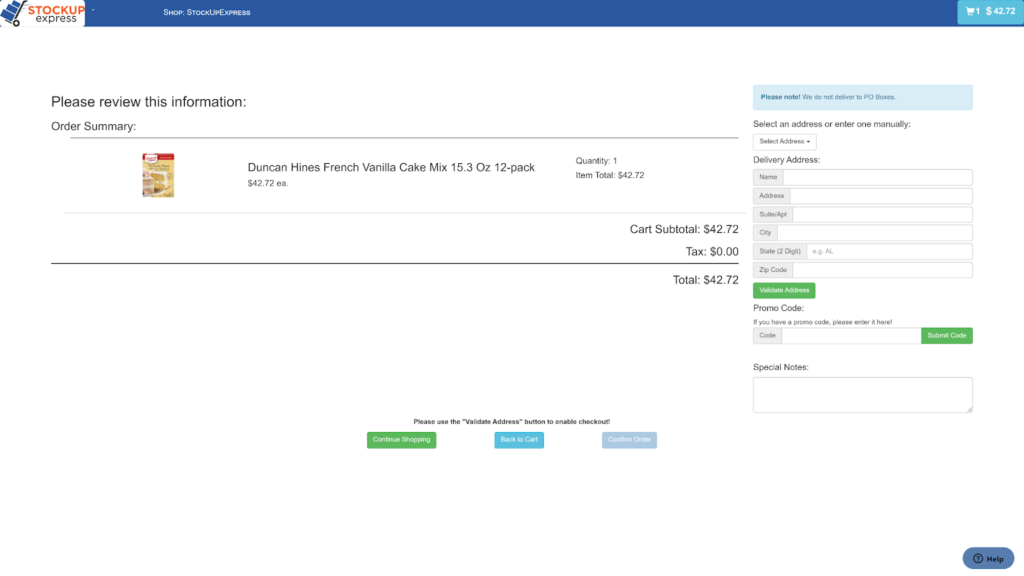
Online grocer, StockUp Express, asks customers to select and validate their address to complete their checkout.
What are the pros and cons of field validation as a defense against spam bots?
Validation processes help your customers and subscribers by preventing errors that may keep them from completing their desired task and help you keep bad information out of your data set. Plus, they may present one obstacle too many for basic bots to get past.
However, real-time validation has the potential to create friction for people, too.
Watch the performance of your validation tools for signs of excessive false alerts or browse abandonments. Also, make sure whatever system you use includes a communication module that tells subscribers what is wrong with their entry and how to fix it.
Add hidden fields or honey pots to catch bots in the act
At some point in your marketing career, you’ve probably learned that hidden or invisible text or other elements in an email or on a web page is a “bad” practice.
Here’s one instance where it isn’t.
Tiny text or same color (invisible) text is sometimes used to add harmful links, stuff keywords, or place other content on a page that is intended only for bots to see–and the practice is considered deceptive.
But in the case of hidden fields as a bot defense, it’s not humans you’re trying to deceive but spam bots. Most bots are programmed to find and fill every field in a form and their programmers don’t take the time to distinguish between visible and invisible ones.
So if you place a field that humans cannot detect in your sign-up form, it serves as a detector for bots. Only automated programs that scan the code of your form to “read” it will fill the hidden field.
It’s a bot honey pot!
The defense uses a simple form of validation, just toss any submission for which the invisible field was completed. (You can also use the IP and other data about the source of these entries to create improved bot defenses.)
This is one of my favorite bot defenses because it doesn’t require your human subscribers to do anything. However, it isn’t a comprehensive solution to the bot problem. Clever coders can instruct their bots to avoid hidden fields.
⚠️Remember that consumers view the totality of their experience with a brand when rating that experience, so even minor points of friction in their journey may hurt your brand reputation. You’ll need to overcome each negative experience with a positive one just to maintain a neutral standing with your customers. This same principle applies to any anti-bot measure that requires user participation or slows their flow.
Spam Bot Deflection Stage 2: List-level defenses against form bots
Use the following tactics to ensure that your current subscription list is spam-free and stays that way:
Scrub your subscription list
Good list hygiene is essential for every successful email marketing program. If your email list hasn’t had a good scrubbing in a while, schedule a bulk email validation session and make sure your list is free of fake emails and spam traps.
To get started, segment your list based on activity. You don’t need to validate subscribers who are actively engaged with your emails.
Next, decide whether you perform a bulk validation to confirm that the addresses are real or simply move them to your suppression list. If a contact has never engaged with one of your emails, is there any reason to keep them on your active list–even if their address is valid?
If you haven’t seen recent activity from a subscriber and want to keep them on your list, perform the validation so that you can be confident in your list’s accuracy going forward.
Systematize your re-engagement and sunsetting processes
After you’re assured that all the email addresses on your active subscription list are valid, implement a sunsetting policy to ensure your list’s continued good health.
Create triggered re-engagement campaigns that will launch when a subscriber has failed to interact with one of your messages for a designated period. Then automate the process of removing subscribers who don’t respond to your re-engagement efforts from your list.
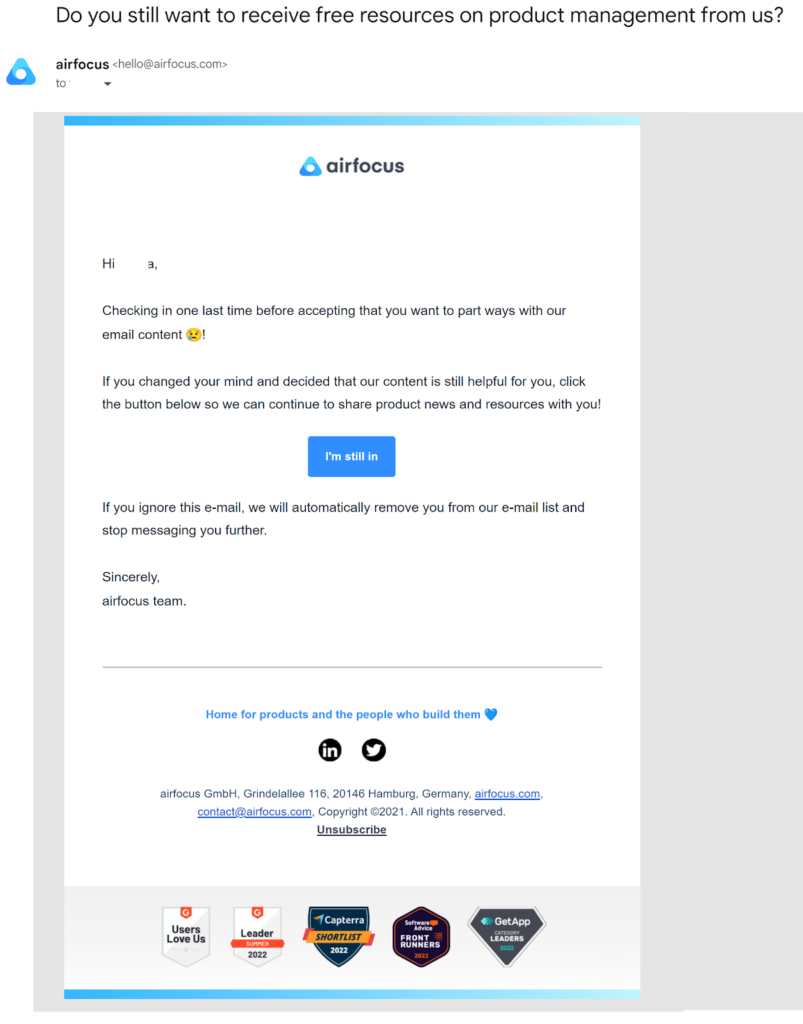
This email from Airfocus encourages its subscriber to stay in touch but also warns that they will be automatically removed from the brand’s email list if they don’t re opt-in.
Confirm the legitimacy of new subscriptions with a double opt-in
Confirmed opt-ins (COIs) are a way for you to ensure that a new subscriber email address is valid and the address’s owner wants to receive your messages.
Double opt-in messages confirm this interest formally by sending a transactional message that asks the new subscriber to confirm their intent to subscribe to your marketing list.
Commercetools sends a confirmation message that asks subscribers to click to complete their subscription and includes an explanation of why the brand is contacting them.
A bonus of the double opt-in system is that it starts your new email relationship off with a click-through that signals engagement to your subscriber’s email service provider.
There is some risk of losing legitimate subscribers when you use a double opt-in to confirm interest. Your message may be overlooked in their inbox or sent to spam. You can reduce the chances of this happening by asking subscribers to be on the lookout for your confirmation message when they sign up.
While a traditional double opt-in email is transactional, you can also increase your chances of gaining a response by including a welcome discount or other reason to click through in your confirmation message.
Similarly, a welcome email with a promised incentive like the one below from beauty supply shop, Hair For the Girls, or important links is a subtle way to get new subscribers to “prove they are human” and interested in your brand by engaging with your message.

Flip the script on form spammers with in-list honey pots
What’s worse than the spam bot you catch? The one you don’t. The longer a breach of your email list goes undetected, the more harm it can cause. Catch incursions early by adding honey pot email addresses to the subscription list.
If a scammer manages to make it past your defenses and steal your email list, they’ll steal these seeded addresses, too.
When the scammer sends messages to your honey pot addresses, you’ll see them. If a message shows up in your seeded email’s dashboard, you’ll know you’ve had a data breach and be able to see exactly what the perpetrators are sending to your subscribers.
Check out Haim’s article for details about how the Hotmark email database defense system works.
Spam Bot Deflection Stage 3: Website-level defenses against form bots
An enterprise anti-bot program must be part of a greater risk management system that ensures the brand’s websites and user data are secure. Add to your network of defenses with these measures:
Block suspicious IPs
Your website’s cybersecurity practices should include routine blocking of known bad IPs or domains. IP blocking can help you cut off bot activity before it starts by preventing traffic from specific addresses from accessing your website or your web forms.
Some website owners choose to block data center IPs which may be used as proxies to disguise the true source of website traffic or IPs for specific geographic regions known to have a high incidence of bot traffic.
Of course, you can probably see the problem with this solution right away. It is a blunt tool that doesn’t distinguish between humans and bots at all. Instead, all traffic is turned away based on a single data point (the IP address).
Deploying such a broad strategy is effectively saying that a particular market’s potential value is too low to invest in alternate bot mitigation strategies. This tactic can not only harm your performance (if your value estimation is wrong) but also alienate your customers within the region and outside of it.
Blocking IPs by region may be justified when required by government regulations or sanctions or when you are defending against or recovering from an extremely damaging bot attack. However, there are more precise methods to keep form bots from filling your subscription list.
One of those methods is IP limiting.
IP limiting may be proactive (blocking known malicious IPs) or responsive (blocking an IP in response to an action on your website).
An example of a responsive limit would be to permit only one form fill, or one form fill within a certain interval per IP. This measure gives every visitor the opportunity to sign up for your subscription list but stops a spam bot from using the same IP to sign up repeatedly.
Applying a one-and-done rule for sign-ups from an IP is the strictest application of this strategy. But this policy may inadvertently block users who are visiting your site from a public computer or shared IP. An interval-based rule won’t keep a bot away permanently. But the imposition of a time limit may force the machine to move on to a new target. (Whether it returns to try again later will depend on the complexity of its code.)
Whether you choose to block many or few, monitor your website traffic and the IPs accessing your forms, to identify problematic addresses. Log blocked traffic to help you learn more about your attackers.
Install web application firewalls
Web application firewalls (WAFs) are a foundational security measure designed to prevent certain types of bot attacks.
Consisting of a set of rules or policies, a WAF is stationed between your website and filters incoming HTTP traffic. The technology may be deployed as a hardware, software or hybrid solution.
The effectiveness of a particular firewall will depend on its design and how often it is updated. For example, a WAF may include a blocklist of domains or IPs, preventing bots originating from those locations from entering your site or filling your forms.
WAFs contribute to your website’s overall security but cannot eliminate every bot threat. This layer of defense should be used along with other methods to keep your site spam bot free.
Expand your defense perimeter with advanced web application defense systems
As bot drivers and bad actors become more advanced, the defense systems website deploy must keep up.
Next-generation firewall (NGFW) and Web application and API protection (WAAP) expand and enhance the defenses of a traditional WAF.
Advanced systems are designed to be adaptive and responsive, protect front end (web applications) and backend (API) protocols, and detect threats across multiple coding languages.
Add anti-bot and bot mitigation systems
While detecting and repelling spam bots before they enter your website is ideal, that doesn’t always happen.
Specialized anti-bot detection and mitigation applications can help identify and boot bots that make it past your front lines. These systems use tactics like user and entity behavior analytics (UEBA) to track the behaviors of website “visitors” and analyze them to assess the likelihood that the actions are those of a human.
Unlike more direct (and simpler) screening mechanisms, these anti-bot mitigation tools are dynamic and adaptive.
They compare each visitor’s actions to a data set of behaviors to identify anomalies. Other factors such as the source of the traffic, known threats and similar characteristics are weighed. The most advanced systems employ machine learning to match the pace of increasingly clever bot designs.
Protect your world with a comprehensive anti-bot defense system that keeps the spam bots out of your business
Preventing form bots from invading your website and your contact list protects your company and your customers.
As you prepare your spam bot defenses, keep your focus on maximizing your data’s security and optimizing your users’ experience.
Put your customers’ needs at the center of your actions and choose bot mitigation methods that don’t inconvenience your subscribers. Remain vigilant. Monitor your metrics for signs of bot activity and add an anti-bot effectiveness review to your email audit list.
After all this talk about bad bots, would you like to learn about some of the good things bots can do for your email marketing program? Hop over to Ayal’s article, How Email Automation Drives Growth, to discover 32 ways automated email campaigns can engage your subscribers and boost your revenue!