Insider threats are the biggest security risk to your organization. There are ways to deal with them, but you’ll have to prepare and take a proactive approach, both on the human and technical sides. Here’s how it’s done.
When we think about data breaches, we often think of shady hackers operating from remote locations.
It’s often more accurate to bring your focus a little closer to home.
Remember the tale of the Trojan Horse?
In the Iliad, Homer tells the tale of the Siege of Troy. For many years, the besieged Trojans managed to defend themselves against the Greek army. Their city had strong walls and fearsome defenders. The Greeks were good fighters, but couldn’t penetrate the city.
The armies were at a stalemate – until cunning Odysseus came up with the famous Wooden Horse tactic.
We all know what happened next.
The Trojans woke up to find the Greek army gone, and a giant wooden horse, standing in front of the city gates. Assuming that the Greeks had left it as an offering for the gods, they took it as a war trophy and dragged it inside the city walls.
The Greeks had hidden soldiers inside the horse, and once the horse reached the city, the trap was set, and at night, the soldiers poured out, opened the gates, and quickly took the city.
Cassandra, the king’s daughter, saw this event happening in one of her visions.
She warned the king, but she was cursed earlier in life by Apollo, the sun god, to see into the future without influencing it.
The king ignored her warnings, and the Greeks won.
The Trojans had done an excellent job of defending their city against threats from the outside, but they had nothing to protect them from the threats inside.
Since then, not much has changed.
Today, companies are aware that a data breach is a likely scenario.
95% of data breaches happen due to human error, and 75% occur due to insider threats, yet everyone tends to ignore it.
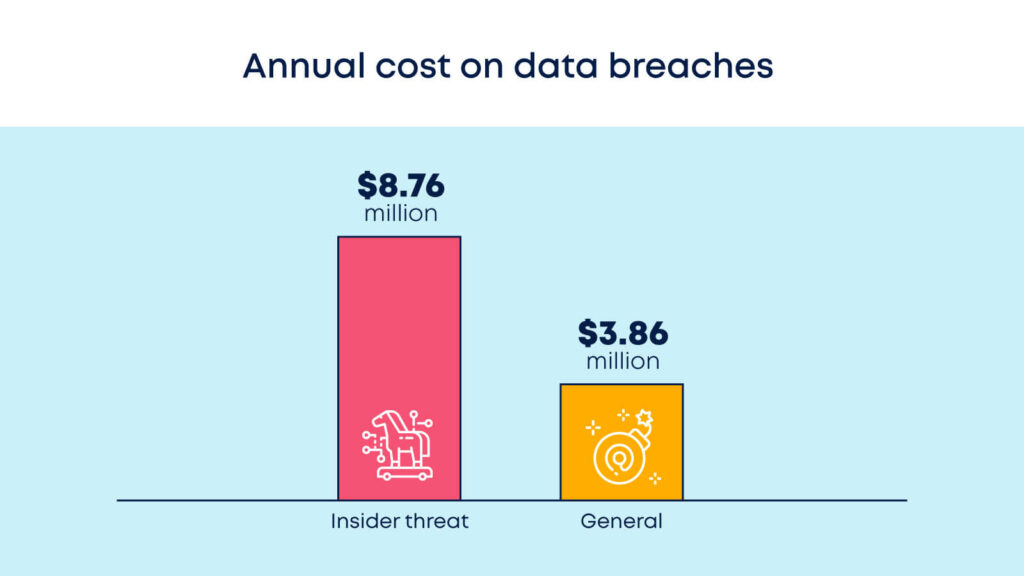
In this Ponemon Institute’s study, researchers found that the average annual cost of an insider threat was $8.76 million.
Compared to the $3.86 million average of data breaches in general, it becomes clear that insider threats pose a massive risk to businesses.
If that’s not enough, Bitglass’s 2019 Insider Threat Report found that insider attacks had become more frequent over the past year. Fifty-nine percent of respondents told Bitglass that their organization had suffered at least one insider attack over the past year.
Insiders already have authorized access to the organization’s information and assets. They typically know where the sensitive data lives within the organization and often have elevated levels of access.
This makes distinguishing between a user’s regular activity and malicious activity a challenge, rendering them all the more dangerous.
What constitutes an insider threat?
In the Trojan horse scenario, the threat came from inside the city. The Trojans were not expecting an attack to be initiated via their newfound trophy, which is why it was so devastatingly effective.
In its simplest form, an insider threat to an organization operates in the same way. An insider threat is a security risk from within the organization. ‘Insiders’ are already past your ‘gates’ (security protocols, firewalls, etc.) and are therefore perfectly positioned to do maximum damage.
Anyone inside your organization can pose a threat, intentionally or not.
An insider can be an employee, officer, or someone else who’s directly involved with the organization at the time of the incident.
Even consultants, former employees, business partners, or board members can pose a threat. Anyone with the necessary capabilities and enough privilege to access data can either cause a very intentional leak or an accidental one.
Yes, not all leaks are intentional.
While it’s intuitive to think of insider threats as malicious by definition, that isn’t always the case.
Not all insider threats are `Greek soldiers’ waiting to pounce on your data. Some are innocent `Trojan citizens’ who simply didn’t understand what they were doing when they let in that ‘horse.’

IBM’s Security Intelligence identifies four main varieties of an insider threat:
Pawns
These are employees who are manipulated into performing malicious activities. This occurs often unintentionally, through spear phishing or social engineering.
A pawn can be an unwitting employee downloading malware to their workstation. Or a user that disclosed credentials to a third party who is pretending to be a help desk employee.
One example involved Ubiquiti Networks, which was a victim of a spear-phishing attack.
Spoofed emails, allegedly from senior executives, were sent to employees. They were then asked to transfer $40 million to a subsidiary’s bank account controlled by fraudsters.
People can be prevented from becoming pawns through:
- Proper training in data protection.
- Running refreshers periodically on security protocols, and even via using enhanced security protocols.
Goofs
Goofs do not act with malicious intent, but they do deliberately undertake potentially harmful actions. As a general rule, Goofs are either ignorant or arrogant – unaware of security policies or thinking that security policies are beneath them.
Goofs are a little more complicated to tackle than Pawns. Unlike Pawns, Goofs are sometimes aware that their actions could be problematic.
- Zero-tolerance policies for poor data practice can help keep Goofs on the straight and narrow, as can stringent and powerful security protocols.
Collaborators
Unlike the above varieties, collaborators do act with malicious intent. They often cooperate with a third party, be it competitors or nation-states, and use their access to harm the organization.
Greg Chung, a Chinese national and former Boeing employee, is an example of a collaborator. He collected documents relating to the space shuttle program and sent them back to China.
Corporate espionage often involves collaborators. Such was the case with Uber and Waymo.
Uber hired a Waymo engineer who was in possession of confidential technology. He then allegedly used it on Uber’s self-driving car project.
Collaborators are often very good at hiding their intentions, so it can be hard to identify them.
- Adding transparency to your data protocols can help to flag collaborator actions before they become damaging.
- Monitoring your data usage via services like Hotmark, which plants honeypots in databases to monitor them in real-time, can help you tackle a breach.
Lone Wolves
A classic example of a lone wolf is Edward Snowden. He used his access to classified systems and leaked information relating to cyber espionage at the NSA.
Lone wolves such as Snowden operate independently and act maliciously. They do so without external influence or manipulation. Coupled with a high level of privileges, they become extremely dangerous.
These four are common forms of insider threats, but they are not the only ones. Here are a few other potential insider threats to be aware of:
Partners
Anyone who has access to your data is a potential insider threat – including your partners. It is important to ensure that your partners have the same training and are subject to the same security protocols as your team.
Disgruntled employees
People who feel a grievance towards your organization are easily persuaded to collaborate with threat actors. They may also act to damage your company of their own accord.
Weak software/systems
Weak or poorly defended software and/or systems may not have human intent behind them – but they are often a gateway through which attacks can be launched. The infamous WannaCry attack on the UK NHS, for example, occurred due to outdated security systems.
When inside threats become attacks

If you want to tackle insider threats effectively, it’s important to understand the forms of attacks and the way they come to be.
There are four main ways in which inside threats turn into devastating data breaches:
Phishing
A targeted individual or all the organization’s employees are contacted via email or text message by someone posing as a legitimate institution. The targeted individuals are then lured into providing sensitive data.
Malware infection
A machine is infected with malicious software (malware). It proceeds to infiltrate the computer, stealing sensitive information or user credentials.
Credential theft
This is a cybercrime that is aimed at stealing the username and password of a targeted individual. Credential theft can be done in various ways, such as the phishing mentioned above and malware infection.
Pass-the-hash
This is a more advanced form of credential theft. The hashed (encrypted or digested) authentication credential is intercepted from one computer. It is then used to gain access to other computers on the network.
How to minimize the risk of insider attacks
There are several ways to reduce the chances of being hit by an insider attack. Each method will have different efficacy for different companies, depending on size and resources.
Employ UEBA (User and Entity Behavior Analytics) – keep an eye out on everyone
One of the more efficient ways to protect yourself from insider threats is by monitoring your employees.
Monitoring employee activity is not videotaping their every move. This might prove as a violation of privacy laws and would create a rigid work environment with disgruntled employees.
Instead, approach this from a behavior-based angle.
UEBA (User and Entity Behavior Analytics) products profile users based on their regular behavior.
With enough historical data, a baseline of normal behavior can be created for each user. It is done by the use of various data points such as access and change-logs.
This baseline indicates the normal operating state of a user or machine so that deviations in this activity can be flagged as abnormal.
Deviations should be tracked not only for a specific user but also compared to other users in the same location, with the same job title or job function.
That way, user-behavior can be modeled, and risk scores can be assigned and tied to specific risky events.
Such events can be:
- Changes in the user’s geographic location.
- Logging in to work at unusual times.
- Downloading to removable media.
- Accessing systems for the first time.
For example, if a user regularly downloads 10MB of files each day, UEBA software will establish this as a baseline behavior. If that user then one day downloads 10GB, the system will recognize this as an anomaly and alert the appropriate person.
It may well be that the user has a perfectly valid reason for increasing their downloads on this particular day. If so, they will be able to explain this and to proceed as normal. However, if they do have malicious intent, the UEBA alert could stop an attack in its tracks.
Provide access only when necessary
Be wary of giving unlimited access to employees, as this is likely to result in a data breach.
Give the wrong people the keys to your Troy, and the Greeks outside the gates may not even need to build a horse to take your company down.
Even if your employee is a pawn or a goof, you’re giving them the power to open the gates and let in threats.
Companies are increasingly turning to Zero Trust networks to ensure that access is only granted when absolutely necessary. For example, Akamai IT transitioned to Zero Trust in 2017 and improved both efficiency and security as a result.
Educate and train your employees
Remember that scandal over the Clinton emails back in 2016? Had the Clinton team been better educated about cybersecurity (particularly phishing), the whole debacle could easily have been avoided.
According to a survey conducted by APAC cybersecurity, 65% of cybersecurity incidents were attributed to internal users making mistakes.
That such a large portion of data breaches was caused by employees who meant no harm actually raises an opportunity. By allocating resources to the education and training of your personnel, it’s possible to reduce the number of attacks significantly.
School your employees about the various types of attack methods, elaborate on the damages they cause, and how they can be avoided.
Further, train them to be vigilant, asking to look out for unorthodox behavior of their peers and reporting them to IT or HR.
Coordinate between HR & IT
As mentioned, on the other end of the pawns and goofs spectrum, there are disgruntled employees with malicious intent.
There are many reasons your staff can become unhappy in the workplace. Perhaps they were skipped over for a promotion, or they don’t feel appreciated.
Many of these cases can and should be spotted by your HR team.
By working closely with your IT team, it’s possible to identify abnormal behavior in high-risk employees and keep closer tabs on these individuals.
Separate and compartmentalize your systems
Secure your operation further by creating a true air-gap between the main network and the organization’s backups or recovery systems.
Doing so ensures that attackers haven’t compromised the backups. This allows IT to safely roll back configurations to their without worrying about further risks.
For example, many oil and gas giants (always a huge risk of cyber attack for financial and activism-related reasons) have recently overhauled their security systems, with separation and compartmentalization as a priority.
They have done this in three stages:
- Defining and isolating their ‘crown jewels’ – these are key data assets that must be protected at all costs. They created libraries for these assets and separated these libraries from the system as a whole.
- Upscaling their security – by creating integrated cybersecurity operations under the care of dedicated CCSOs (Chief CyberSecurity Officers), they enhanced their capability to spot and react to threats as they occurred.
- Implementing a long-term plan – Moving forward, the oil and gas giants have implemented a plan involving frequent check-ups and upgrades, which may possibly include further degrees of separation and compartmentalization in the future.
Keep your data safe from insider threats
Compared to external breaches, insider threats hit businesses much harder in terms of revenue loss, and their occurrence rises each year.
There are several ways to reduce the prospect of being attacked. Companies should invest as many resources as possible in order to do so.
But even if you implement everything we’ve suggested above, a breach may happen one day.
That’s why it’s imperative to have a solid action plan, a CSIRP, for when that day comes.
The way you react to the (sometimes inevitable) breach is at least equally as important as trying to prevent it.
Here’s what you need to do after a data breach happened.
Troy is a tragic tale with a moral we all can learn from. Keep your guard, stay prepared, and be proactive.